0 Results for ""
Identity Crisis: Breaking Down The Emerging Identity Stack
The Identity Problem
Almost every major modern security incident can be traced back to an identity problem. Just look at the data:
- Malware-free, identity-centric attacks increased from 40% to 75% of incidents between 2019- 2023[1]
- 68% of breaches involve a non-malicious human element, like a person falling victim to a social engineering attack[2]
- 80% of attacks use Active Directory for lateral movement and privilege escalation[3]
In short, exploiting trusted relationships has become the norm for attackers.
The security industry has innovated rapidly as new infrastructure has emerged. As cybercriminals began to exploit new attack vectors, startups built new solutions to secure cloud infrastructure, data, and APIs. In turn, the success of those products exposed the identity stack as a key organizational weakness. The difficulty of achieving true zero trust (i.e. no inherently trusted pathways, continuous authentication for every service/user) means that every slip up at the infrastructure level, every weakness in employee security awareness, and every exposed unused entitlement carries a greater cost than ever before. In effect, identity challenges are amplifying the challenges of every other security category.
It doesn’t look like the problem will get any better in the near term. Generative AI is increasing human risk by lowering the barrier to entry for sophisticated phishing attacks. And the increasingly dynamic nature of companies, in which employees join, leave, and shift responsibilities more frequently, only exacerbates the risk. The end of the perimeter requires a holistic and fundamentally new set of principles and practices.
Unlike in other parts of security, creating and implementing a robust identity program can feel like reinventing the wheel for security practitioners. Every company looks a little different, making it hard for CISOs to establish and rely on industry-wide best practices.
Breaking down the Identity Landscape
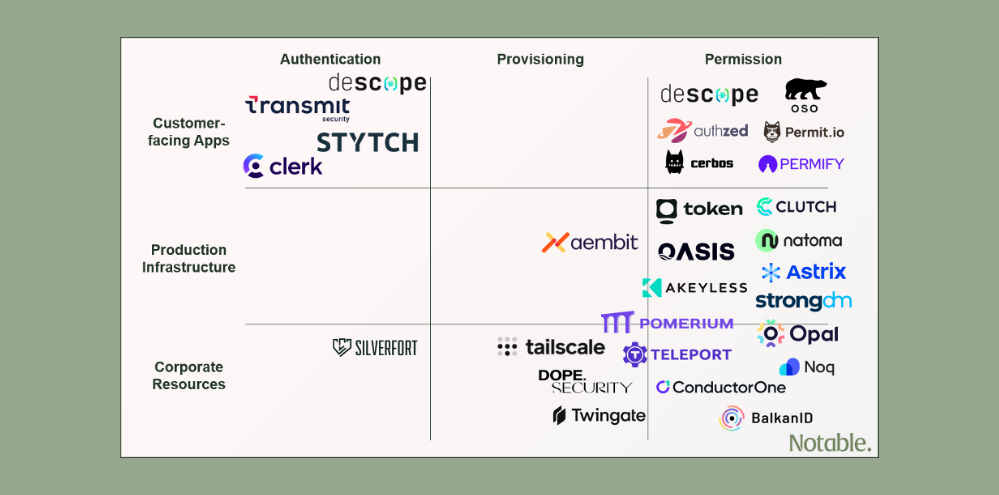
As the perimeter dissolved and companies have attempted to move to a zero-trust architecture, we’ve seen companies build their identity strategies across a few vectors. We’ve attempted to simplify that strategy into a matrix of the use cases enterprises need to secure and the tools they have to secure them.
Use Cases: With the advent of the cloud, companies need to secure a wider variety of resources than ever. We split them up by the focus of each.
- Customer-facing Apps: Apps the company builds for customers or other non-employees
- Production Infrastructure: Resources developers touch to build customer-facing apps; deployed either as PaaS, IaaS, or on-prem
- Corporate: Internally used SaaS, on-prem apps, and endpoints
Tools: The toolset for managing identities breaks down into who needs access, how they are accessing a resource, and what resources they can access.
- Authentication (who): Authentication tools determine whether an identity can access a resource
- Provisioning (how): Provisioning tools provide the rails for the identity to actually access that resource
- Permissions (what/when): Policy/permissions tools contain the logic of which identities can access which resources, to what extent, and for how long
In simpler terms, Authentication decides if you can get in the front door, Provisioning opens the door and brings you to your destination, and Permissions controls where you can roam once inside and for how long.
Incumbent products in the identity space generally map to one of these cross-sections, at least as a starting point (though with consolidation, many companies have expanded to multiple resources and tools). For a large enterprise, each of these boxes can represent a seven or even eight-figure spend item.

Importantly, these resources can be accessed via both human and non-human identities, often through different tooling. For the sake of simplicity, we’re taking a high-level view of the problem.
Where has value been created?
What’s particularly striking here is that the lion’s share of the value in identity to date (outside of Microsoft) has been created at the provisioning layers. Okta ($12B market cap), Cloudflare ($29B), Zscaler ($26B), CyberArk ($12B), Hashicorp Vault* ($7.7B), and Ping Identity ($2.8B acquisition), each generate hundreds of millions to billions of ARR, are most simply defined as the pipes that enable access. That alone created multi-billion-dollar businesses, as they are the required foundation for any identity strategy. After all, even the best policies aren’t worth much if you don’t have the infrastructure to implement them.
These former startups have also had to deal with the challenges of company maturity. Many have been consolidated, sometimes by private equity, while others have had to cope with the pressures of impatient public market investors. Customer needs are falling by the wayside.
All the while, the recent run of attacks has demonstrates that security teams need more than identity infrastructure alone to build a robust security program. The pertinent question today is no longer, “how do I enable and disable access?” it’s “how do I continuously ensure I know users/services are who they say they are?” and “what should those users/services have access to and under what conditions?” all while enabling productivity of business and engineering teams.
New Opportunities
We believe there’s a tremendous opportunity for startups to help companies of all sizes across the identity stack. A few categories stand out:
Customer-Facing Authentication.
Until recently, most companies had to choose between Auth0 and homegrown solutions to authenticate their end users. We hear consistent frustration with both; Auth0 has become expensive and inflexible, and DIY approaches are costly to maintain.
New companies like Descope*, Clerk, and Stytch offer much more developer-friendly and flexible auth solutions that incorporate secure, passwordless approaches. These tools enhance security and improve user experience by streamlining the development process. By simplifying the creation and maintenance of secure user flows, they reduce friction that impact customer satisfaction while maximizing developer flexibility. Additionally, these products are evolving to include authorization features, allowing companies to define and enforce policies within the same platform.
Next-generation IGA/PAM.
Even for companies who can enforce policy, determining identity policy is extremely difficult, particularly as they move to least privileged approaches. Enterprises today recognize that they over permission. But for most CISOs the consequences of over permissioning come rarely and the consequences of under permissioning come in a near-daily barrage of angry emails from engineers and business users.
We’re seeing a new wave of startups go after traditional IGA vendors offering more intelligent policies and workflow orchestration approaches. This can include pulling context from customer environments to see what users actually use in order to right-size permissions, and slicker workflows for just-in-time access. A context-centric approach should support a zero-trust security model while improving operational agility. In the future, these products can use the same foundations to expand into PAM, giving security teams a centralized way to control policy across users and admins of both production infrastructure and corporate resources. Companies like Pomerium, StrongDM, Valkyrie, Opal, ConductorOne, Teleport, and Veza are blurring the line between policy and provisioning in order to help CISOs achieve their goals without aggravating their colleagues.
Non-Human Identity.
As companies moved to the cloud, the number of non-human identities (e.g. secrets, API tokens) with access to important resources ballooned. Some companies have estimated they have 45x more non-human than human identities. Hashicorp’s Vault* has emerged as the standard for storing and provisioning those credentials across cloud environments, but NHIs tend to be distributed across IAM technologies, especially in hybrid environments. Such complexity means that managing the NHI lifecycle is particularly risky.
A new crop of startups is emerging to solve the full lifecycle of non-human identities (NHIs), effectively becoming IGA solutions for modern cloud environments. This means both ensuring security teams understand the existing scope of their NHIs and enforce best practices like least privilege, key rotation, ownership, and retirement of NHIs that are no longer in use. Companies in this space, like Token, Oasis, Clutch, and Natoma are aiming to reduce the attack surface for potential hacks by preventing lateral movement via NHIs. We see an opportunity to expand and become an “Okta for services,” by actually acting as an identity provider for NHIs, provisioning those identities only when they are required, and then governing with full knowledge and control of their scope.
The Agent Problem.
To add to security team’s headaches, rapid innovation in AI is quickly creating a new set of identity problems. Enterprise search tools and internal chatbots require widespread, up to date RBAC (or even ReBAC) to be implemented across existing systems to avoid accidentally exposing sensitive data to the wrong users.
The next phase of the LLM revolution—continuous, independent agents that take action on behalf of users/companies—will exacerbate the NHI governance issue by introducing non-deterministic services to many critical systems. Beyond making NHI security more critical, the rise of agents necessitates new approaches to authorization. Rather than waiting for agents’ actions to become 100% predictable, companies can limit the scope of what an agent can do within their apps, thereby limiting their potential negative impacts. In practice, this could mean introducing new identity types within applications that are more permissive than an API but have more guardrails than a human identity, allowing enterprises to benefit from agents without risking their critical systems.
The Emerging Startup Ecosystem
Identity today is simultaneously the biggest opportunity in security and the most challenging place to build a hyper-growth security startup. Improving identity posture is one of the most impactful things a CISO can do; yet, high cost of failure and difficult implementation prevents great solutions from being adopted quickly. Finding a compelling wedge and a smooth expansion motion is critical.
The increasing but still limited authority of CISOs also presents unique challenges. We’re seeing more and more CISOs owning IT, giving them broad authority over identity tools in Corporate Resource use cases. CISO’s authority over developer and production environments is more restricted, leading startups serving Customer-facing Apps and Production Infrastructure use cases to take a more dev-centric approach.
Thankfully, we’re seeing dozens of fantastic founders step up to the challenge. The identity ecosystem is more vibrant than ever:

At Notable Capital, we’ve had the privilege of working with security companies like Drata, Orca Security, Torq, Gem Security, Nozomi, Wing Security, and Descope from their earliest days. If you’re disrupting the identity stack or thinking of innovating in this space, we’d love to hear from you.
Thank you to Al Ghous, Bobby DeSimone, Ido Shlomo, Itamar Apelblat, Rishi Bhargava, Ty Sbano, Umaimah Khan, and our colleagues Glenn Solomon and Laura Hamilton for providing guidance and feedback on this blog post.
[1] CrowdStrike Global Threat Report
[2] Verizon 2024 Data Breach Investigation
[3] Tenable, Secure Active Directory and Disrupt Attack Paths
*Indicates a Notable Capital portfolio company





.jpg)